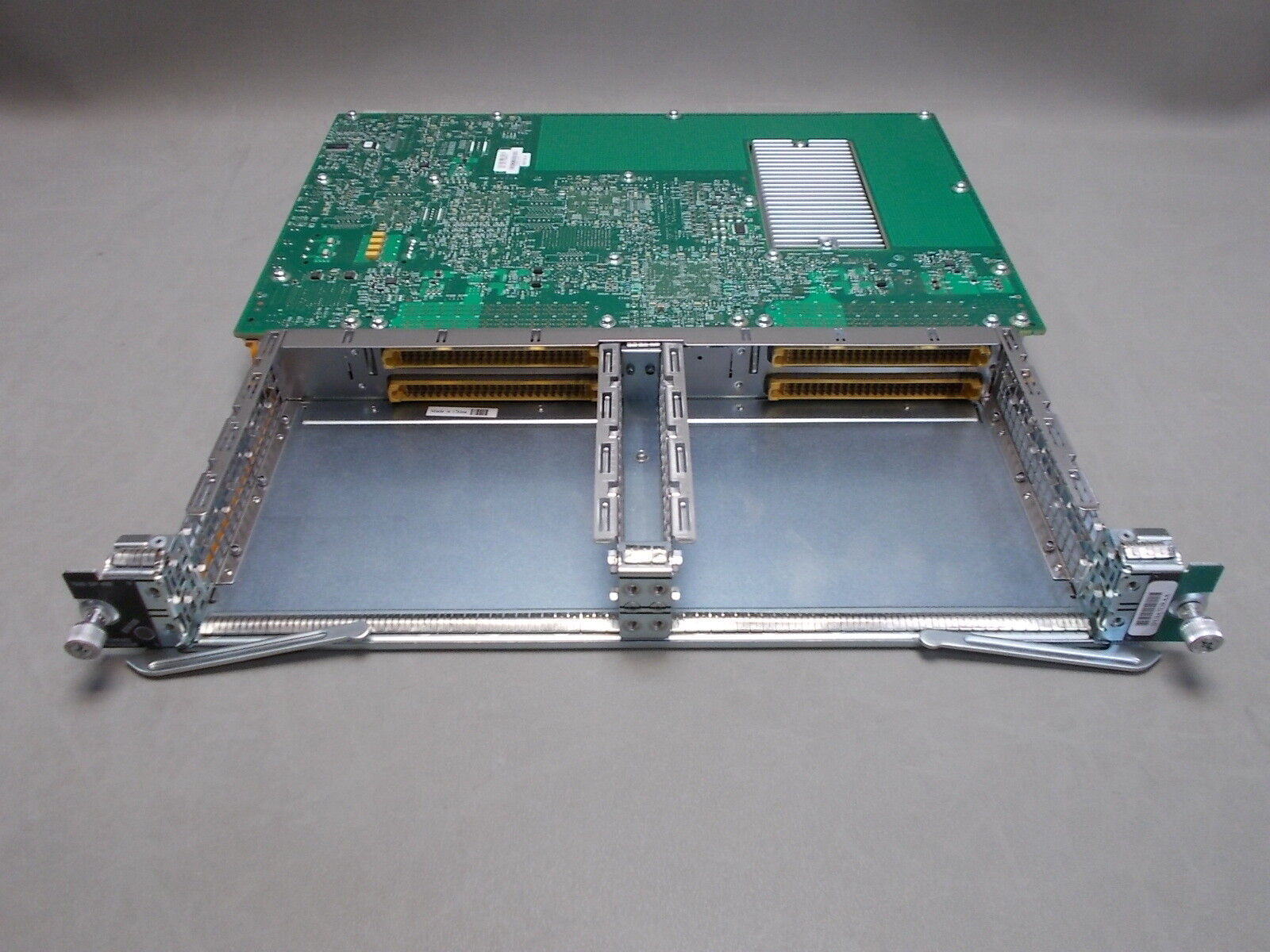
Cisco 7600-SIP-400 Cisco 7600 Series SPA Interface Processor-400 68-1920-19 For Sale
When you click on links to various merchants on this site and make a purchase, this can result in this site earning a commission. Affiliate programs and affiliations include, but are not limited to, the eBay Partner Network.
Cisco 7600-SIP-400 Cisco 7600 Series SPA Interface Processor-400 68-1920-19 :
$90.30
PART#:7600-SIP-400ALTERNATIVE PART #s:68-1920-19&IPUIA7D
DESCRIPTION:The Cisco®I-Flex design combines shared port adapters (SPAs) and SPA interface processors (SIPs), offering an extensible design that enables service prioritization for data, voice, and video services. Enterprise and service provider customers can take advantage of improved slot economics resulting from modular port adapters that are interchangeable across Cisco routing platforms. The I-Flex design maximizes connectivity options and offers superior service intelligence through programmable interface processors that deliver line-rate performance. The interface processors help accelerate service delivery and revenues and provide a rich set of quality-of-service (QoS) features for premium service delivery.
MANUFACTURER:CISCO
CONDITION:KEY TESTED. This equipment will be key tested before it ships to you, pleaseallow 24 hrs for us to complete this process.
Pleasenote: No other accessories, parts, cables, manuals, etc. are included besideswhat you see in the photograph(s)
WARRANTY:30 DAYS
EQUIPMENTIS SAFELY PACKAGED USING ESD STANDARDS IN OUR ISO 9000/TL 9000 REGISTEREDFACILITY
PLEASECONTACT US IF YOU HAVE ANY QUESTIONS
The following R2:2013 equipment conditions apply depending on the description of the item listed: (a) Items described as NEW or TESTED are considered to be “Tested for Full Functions, R2/Ready for Reuse” under the R2:2013 standard;(b) Items described as KEY TESTED are considered to be “Tested for Key Functions, R2/Ready for Resale under the R2:2013 standard;and (c) Items described as UNTESTED, KNOWN DEFECTIVE, or DAMAGED, are considered to be “Evaluated and Non-Functioning, R2/Ready for Repair” under the R2:2013 standard;If the equipment has been tested for key functions, Sector Supply can provide a copy of the test out sheet for said equipment upon request, detailing the test results for each unit in the purchase. If KEY TESTED equipment has any key test failures, this will be made known to the purchaser by describing such failures in the listing itself;and any equipment being purchased without either full or key functions testing (e.g., UNTESTED, KNOWN DEFECTIVE, or DAMAGED) is understood to be sold for reuse, repair, and refurbishment only. UNTESTED purchases will require customer qualification prior to shipment (see preview of the agreement you will be asked to sign in listing)1;KNOWN DEFECTIVE or DAMAGED purchases will require a complete downstream vendor audit package prior to shipment – we will contact you to proceed. All purchases of UNTESTED, KNOWN DEFECTIVE or DAMAGED product is subject to annual verification of the product’s disposition, meaning you agree to respond to Sector Supply with information and documentation (redacted shipping docs, etc) upon request.
Track Page Views With
Auctiva's FREE Counter

Related Items:
CISCO 7600-SIP-200 68-2630-02 SPA INTERFACE PROCESSOR SIP 200 7600 FAMILY
$34.00
Cisco 7600-SIP-400 Cisco 7600 Series SPA Interface Processor-400 68-1920-19
$90.30
CISCO 7600-SIP-200 68-2630-03 SPA INTERFACE PROCESSOR SIP 200
$72.24
![]()
Documentation
- AIX Local Security Checks
- Backdoors
- CentOS Local Security Checks
- CGI abuses
- CISCO
- Databases
- Debian Local Security Checks
- Default Unix Accounts
- Denial of Service
- Fedora Local Security Checks
- Finger abuses
- Firewalls
- FreeBSD Local Security Checks


